北京大学 CECA 深度学习加速器
https://www.bilibili.com/video/BV1ih411o7Yy
PYNQ-Z1 中文指导手册
https://digilent-china.gitbook.io/pynq-z1_tutorial/
CS-143 斯坦福编译原理
北京大学 CECA 深度学习加速器
https://www.bilibili.com/video/BV1ih411o7Yy
PYNQ-Z1 中文指导手册
https://digilent-china.gitbook.io/pynq-z1_tutorial/
CS-143 斯坦福编译原理
Hi, there!
Now My blog site is loaded with SSL certificate , which use Let’s Encrypy free service.
最近在使用PYNQ,Jetson Nano进行一些开发,但是迫于实验室需要外接校园网、使用图形页面登陆所以嵌入式设备无法直接上网。本文给出的解决方案是将嵌入式设备通过以太网连接到个人主机上,然后将以太网桥接到 Wifi,访问因特网。
我分别在Ubuntu20.04与Windows10上实践了两方案,核心只有两句话,网线接 lan 口,关了 dhcp。
你需要准备的:
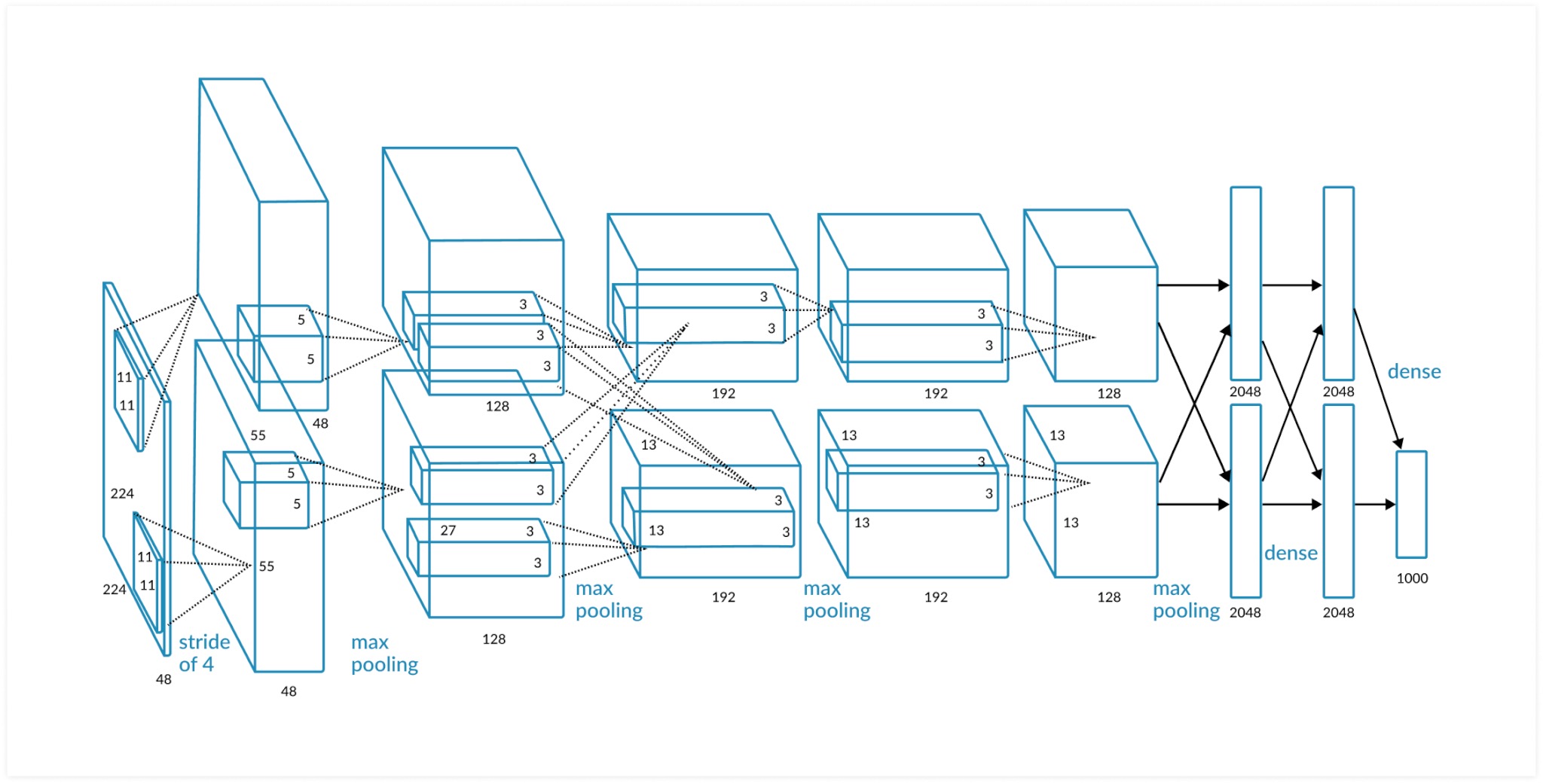
在这篇博客,我使用 Pytorch 构建了一个 AlexNet 网络,通过 flower_data 数据集训练 AlexNet 识别各种花朵,然后我分别使用 pytorch 直接推理网络,以及使用 tvm 编译过后的模型推理网络,对比了两者的输出,以及运行的速度。
Github Page:https://github.com/LeiWang1999/AlexNetTVM
Update your browser to view this website correctly. Update my browser now